There was a tweet yesterday by Eric Mill (@konclone) where he posted a copy of bug 1348902 filled with Mozilla. It has been made private presumably to cut down on trolling. Here is a screen shot:
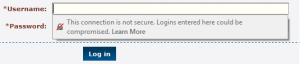
For those that don’t know FireFox (and coming soon to Chrome) have now built in that if you are asked to enter a password on a page that does not have an ssl it will throw an error like this
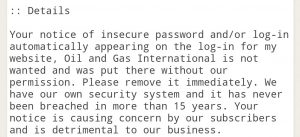
This is to let the user now that their credentials are going to be sent over the internet insecurely. If their traffic is being proxied or worse some one is listening in they will easily get your credentials. Rather than the developer add an SSL cert which is free today thanks to Let’s Encrypt the developer opened a ticket with Mozilla asking that this detrimental feature be removed. It’s fairly evident that the developer has very little to no opsec experience and it’s amazing that they were not compromised till now. What a can of worms s/he opened. Here is a list of issues that were found by several twitter users.
- The SQL queries were not sanitized and good ole Bobby Tables (more on that here) paid them a visit. You can see from this screen shot
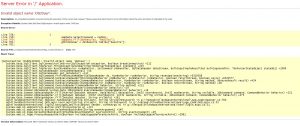
that the table it’s using to find the user no longer exists. - Next try entering some letters where the corp ID should be. Why are you assuming that the user will enter it correctly.
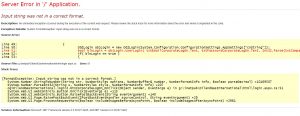
- Looking at the error pages above you can see the .Net version is 2.0.X. As per Wikipedia 2.0 was released in 2005!
The list goes on and on. I am in complete shock! On the bright side this I guess this can be filed under job security.
EDIT: A lot more has happened (unprotected windows share, information extracted them dumped etc.) since then including the site being taken off line. You can read more about on the reddit thread here: https://www.reddit.com/r/programming/comments/60jc69/company_with_an_httpserved_login_form_filed_a/
Leave a comment